Top Stories
Perplexity Denies Comet Browser Vulnerability Claims Amid Controversy

BREAKING: Perplexity is facing serious allegations over a potential vulnerability in its Comet browser, as cybersecurity firm SquareX claims that a hidden MCP API could allow unauthorized command execution. In a swift rebuttal, Perplexity branded these accusations as “entirely false” and part of a growing issue of “fake security research.”
The controversy erupted when SquareX asserted it discovered a hidden API within Comet capable of executing local commands on users’ devices. This API, identified as the MCP API, allegedly allows embedded extensions to perform actions that traditional browsers strictly prohibit. SquareX claimed that this vulnerability could be exploited if the perplexity.ai page were compromised, potentially threatening user security across the board.
In response, Jesse Dwyer, a spokesperson for Perplexity, stated, “The report is entirely false,” emphasizing that exploiting this vulnerability requires users to first enable developer mode and manually sideload any malicious software. “To replicate this, the human user must turn on developer mode and manually sideload malware into Comet,” Dwyer added.
SquareX’s Kabilan Sakthivel criticized Perplexity’s response, arguing that ignoring established security protocols undermines decades of browser security advancements made by major vendors like Chrome and Firefox. However, Dwyer contends that user consent is always required for any local system access, asserting, “When installing local MCPs, we require user consent—users are the ones setting it up and calling the MCP API.”
In a dramatic twist, SquareX claimed that Perplexity updated the Comet browser shortly after their proof-of-concept demonstration, leading to new statements that “Local MCP is not enabled.” They also reported that three external researchers successfully replicated their findings. “This is excellent news from a security perspective, and we are glad that our research could contribute to making the AI Browser safer,” the company stated.
Perplexity accused SquareX of failing to provide a proper report, claiming they only received a link to a Google Document without context or access. “We informed them we were unable to open the Google docs, requested access, and never heard back,” Dwyer explained.
As the situation develops, users of the Comet browser are urged to remain vigilant and ensure they are updated with the latest security measures. This unfolding situation highlights the constant battle between cybersecurity firms and tech companies, raising critical questions about user safety and data protection in digital environments.
Expect further updates as both companies continue to address these serious allegations. The cybersecurity community is closely monitoring the developments, with significant implications for users of the Comet browser and the broader tech landscape.
Stay tuned for more urgent updates on this story.
-

 Science4 weeks ago
Science4 weeks agoUniversity of Hawaiʻi at Mānoa Joins $25.6M AI Initiative for Disaster Monitoring
-

 Science2 months ago
Science2 months agoIROS 2025 to Showcase Cutting-Edge Robotics Innovations in China
-
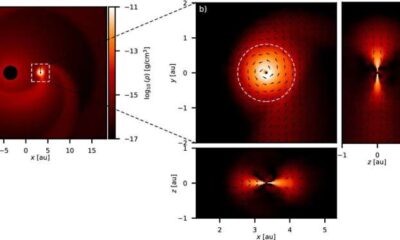
 Science2 weeks ago
Science2 weeks agoALMA Discovers Companion Orbiting Red Giant Star π 1 Gruis
-

 Lifestyle2 months ago
Lifestyle2 months agoStone Island’s Logo Worn by Extremists Sparks Brand Dilemma
-

 Health2 months ago
Health2 months agoStartup Liberate Bio Secures $31 Million for Next-Gen Therapies
-

 Lifestyle2 months ago
Lifestyle2 months agoMary Morgan Jackson Crowned Little Miss National Peanut Festival 2025
-

 World2 months ago
World2 months agoBravo Company Veterans Honored with Bronze Medals After 56 Years
-

 Politics2 months ago
Politics2 months agoJudge Considers Dismissal of Chelsea Housing Case Citing AI Flaws
-
 Health2 months ago
Health2 months agoTop Hyaluronic Acid Serums for Radiant Skin in 2025
-

 Science2 months ago
Science2 months agoArizona State University Transforms Programming Education Approach
-

 Sports2 months ago
Sports2 months agoYamamoto’s Mastery Leads Dodgers to 5-1 Victory in NLCS Game 2
-

 Sports2 months ago
Sports2 months agoMel Kiper Jr. Reveals Top 25 Prospects for 2026 NFL Draft







